
Computer Applications
A complete study about computer.
Wednesday, 19 October 2016
CHAPTER 14
ENTERPRISE COMPUTING
Enterprise computing is a buzzword that refers to business-oriented information technology that is critical to a company's operations. It involves the use of computers in networks, such as LANs and WANs (Wide Area Network), or a series of interconnected networks that encompasses a variety of different operating systems, protocols and network architectures.
Types of enterprises:
Human resources
Enterprise computing is a buzzword that refers to business-oriented information technology that is critical to a company's operations. It involves the use of computers in networks, such as LANs and WANs (Wide Area Network), or a series of interconnected networks that encompasses a variety of different operating systems, protocols and network architectures.
Types of enterprises:
- Retail.
- Manufacturing.
- Service.
- Wholesale.
- Government.
- Educational.
- Transportation.
In an enterprise, users typically fall into one of four categories:
- Executive management
- Middle management
- Operational management
- non-management employees.
Enterprise information is the information gathered in the ongoing operations of an enterprise-sized organization
- Business intelligence
- Business process management
- Business process automation
Managers coordinate resources by performing four activities:
- Planning
- Organising
- Leading
- Controlling.
An information system is a set of hardware, software, data, people, and procedures that work together to produce information.
Enterprises
Accounting and finance
- Accounting software- manages everyday transaction.
- Billing software- reconcile purchases with customer payments.
- Financial software- helps managers budget, forecast and analyse.
Human resources
- A human resources information system (HRIS) manages one or more human resources functions
- Employee relationship management systems manage communication between employees and the business
- Computer-aided design (CAD) uses a computer and special software to aid in engineering, drafting, and design
- Computer-aided engineering (CAE) uses computers to test product designs
- Computer-aided manufacturing (CAM) is the use of computers to control production equipment
- Computer-integrated manufacturing (CIM) uses computers to integrate the many different operations of the manufacturing process
- Material Requirements Planning (MRP)- uses software to help monitor and control processes related to production.
- Manufacturing Resource Planning II (MRP II)- is an extension of MRP and also includes software that helps in scheduling.
- Quality Control System- helps an organisation maintain or improve the quality of its products or services.
- Marketing Information System- serves as a central repository for the tasks of a marketing department.
- Sales force automation (SFA) software equips traveling salespeople with the electronic tools they need to be more productive
- provide forecasting for inventory control
- manage and track shipping of products
- provide information and analysis on inventory in a warehouse.
- Customer interaction management (CIM) software manages the day-to-day interactions with customers
- The information technology (IT) department makes technology decisions for the enterprise
- Whether to build or buy new information systems
- When a computer or information system has outlived its useful life
- Web site management programs collect data designed to help organizations make informed decisions regarding their Web presence
- Office Information System (OIS)- oriented to word processing, electronic mail and other similar office functions.
- Transaction Processing System (TPS)- for business transactions involving the collection, modification and retrieval of all transaction data.
- Management Information System (MIS)- focuses on management of information systems to provide efficiency and effectiveness of strategic decision making.
- Decision Support System (DSS)- a set of related computer programs and data required to assists with analysis and decision making within an organisation.
- Expert System- a piece of software programmed using artificial intelligence. It uses database of expert knowledge to offer advice or make decision. For example, it is the help button found in our operating system.
- Integrated Information System (IIS)- an array of multiple information sets linked together in an organised way.
Technologies used in enterprise:
- a collection of links, content and services presented on a Web page that are interesting for a particular job function/
- a huge database that stores and manages the data required to analyse historical and current transactions.
- a set of standards that control the transfer of business data and information among computers both within and among enterprise.
- a portion of a company's network that allows customers or suppliers of a company to access parts of an enterprise's intranet.
- allow businesses to create products and B2B interactions over the Internet.
- allows for storage and management of a company's documents.
- a defined process that identifies the specific set of steps involved in completing a particular project or business process.
- allow customers or vendors to connect to company network server in a private network connection.
Enterprise hardware allows large organizations to manage and store information and data using devices geared for:
- Heavy use
- Maximum availability
- Maximum efficiency
RAID duplicates data and implements duplication in different ways.
Network attached storage (NAS) is a server that provides storage to users and information systems attached to the network
A storage area network (SAN) is a high-speed network that provides storage to other servers to which it is attached
An enterprise storage system is a strategy that focuses on the availability, protection, organization, and backup of storage in a company.
A blade server packs a complete computer server on a single card (called a blade) rather than a system unit.
A thin client is a small terminal-like computer that mostly relies on a server for data storage and processing
Backup Procedures
- Full- fastest recovery method.
- Differential
- Incremental
- Selective
- Continuous
A disaster recovery plan is a written plan describing the steps a company would take to restore computer operations in the event of a disaster
Contains four major components
- Emergency plan
- Backup plan
- Recovery plan
- Test plan
CHAPTER 13
COMPUTER PROGRAM AND PROGRAMMING LANGUAGES
A computer program is a series of instructions that directs a computer to perform tasks
A computer program is a series of instructions that directs a computer to perform tasks
- Created by a programmer using a programming language
Low level languages
Machine language is the first generation of programming languages
- Only language the computer directly recognizes
Assembly language is the second generation of programming languages
A source program contains the code to be converted to machine language
Procedural languages- instructions that tell computer what and how to do.
- Third generation language- a compiler translates an entire program before executing it, and an interpreter converts and executes one code statement at a time.
- C programming language- used to write many of today's programs.
- COBOL (COmmon Business Oriented Language)- designed for business application with easy to read English like statements.
Object oriented programming languages- allow reuse and modification of existing object.
Advantages
- objects can be reused,
- programmers create applications faster,
- work well in RAD (Rapid Application Development) environment
- most program development tools are IDEs (Integrated Development Environment).
Examples
- Java- an object oriented programming language developed by Sun Microsystem.
- Just In Time (JIT) compiler converts byte code into machine dependent code.
2) Microsoft .NET framework- allows almost any type of program to run on the Internet or an internal business network, as well as computers and mobile devices.
- Features include CLR (Common Language Runtime) and Classes.
3) C++
- an extension of C programming language.
4) C#
- based on C++ and was developed by Microsoft.
5) F#
- combines the benefit of an object oriented language with those of a functional language.
6) Visual studio
- Microsoft suite's of program development tools.
PowerBuilder is a powerful program development RAD tool
Best suited for Web-based, .NET, and large-scale enterprise object-oriented applications.
A 4GL (fourth-generation language) is a nonprocedural language that enables users and programmers to access data in a database
- One popular 4GL is SQL
Classic programming languages:
- Ada
- ALGOL
- APL
- BASIC
- Forth
- FORTRAN
- Hyper Talk
- LISP
- Logo
- Modula-2
- Pascal
- PILOT
- PL/1
- Prolog
- RPG
- Small Talk
Application generator
- a program that creates source code or machine code from a specification of the required functionality. Often bundled as part of DBMS (Database Management System).
Macro
- a series of statements that instructs an application how to complete a task. Can be created in two ways, record the macro with macro recorder and write the macro.
Web Page Development
- HTML is a special formatting language that programmers use to format documents for display on the Web
- XHTML is a markup language that allows Web sites to be displayed more easily on mobile devices
- WML is a subset of XML and is used to design pages for microbrowsers
- XML allows Web developers to create customized tags and use predefined tags to display content appropriately on various devices
Two applications of XML are RSS 2.0 and ATOM
Various languages that are used to write Scripts, Applets, Servlets and ActiveX controls.
For example:
- Java Script.
- Perl.
- PHP (Hypertext Preprocessor).
- Rexx
- Tcl.
- VBScript.
Dynamic HTML (DHTML)
- allows web developers to include more graphical interest and interactivity.
CSS (Cascading Style Sheets)
- contains the formats for how a particular objects should be displayed.
Ruby on Rails (RoR)
- provide technologies for developing object oriented, database driven web sites.
Web 2.0
- allows web sites to provide a means for users to share personal information, modify web site content and it has application software built into the site.
API (Application Program Interface)
- a set of routines, protocols and tools for building software applications. It specifies how software components should interact.
Web page authoring software
- can create sophisticated web pages that include images, video, audio, animation and other effects.
Example:
- Dreamweaver.
- Expression Web.
- Flash.
- Share Point Designer.
Multimedia program development
Multimedia authoring software
- allows programmers to combine text, graphics, animation, audio and video in an interactive presentation.
Example:
- Tool Book.
- Director.
Program development
- consists of a series of steps programmers use to build computer programs.
Steps
Analyze requirement
- Reviews the requirements
- Meets with the systems analyst and users
- Identifies input, processing, and output
- IPO chart
Design solution
- Design a solution algorithm
- In structured design, the programmer typically begins with a general design and moves toward a more detailed design
- Programmers use a hierarchy chart to show program modules graphically
- With object-oriented (OO) design, the programmer packages the data and the program into a single object
- The sequence control structure shows one or more actions following each other in order
- The selection control structure tells the program which action to take, based on a certain condition
- The repetition control structure enables a program to perform one or more actions repeatedly as long as a certain condition is met
- A program flowchart graphically shows the logic in a solution algorithm
- Flowcharting software makes it easy to modify and update flowcharts
- Pseudocode uses a condensed form of English to convey program logic
- UML (Unified Modeling Language) has been adopted as a standard notation for object modeling and development
Check for logic errors using test data
- Develop various sets of test data
- Determine the expected result
- Step through the algorithm
- Compare the results
- Repeat steps for each set of test data
Implement design
Implementation of the design includes using a program development tool that assists the programmer by:
- Generating or providing some or all code
- Writing the code that translates the design into a computer program
- Creating the user interface
Test solution
The goal of program testing is to ensure the program runs correctly and is error free
- Errors include syntax errors and logic errors
- Debugging the program involves removing the bugs
- A beta is a program that has most or all of its features and functionality implemented
- Review the program code.
- Review all the documentation
CHAPTER 12
EXPLORING INFORMATION SYSTEM DEVELOPMENT
System development is the development of an information system. System is a set of components that interact to achieve a common goal. System development should involve representatives from each department in which the proposed system will be used.
Information system is a collection of hardware, software, data, people and procedures that work together to produce quality information.

System development is the development of an information system. System is a set of components that interact to achieve a common goal. System development should involve representatives from each department in which the proposed system will be used.
Information system is a collection of hardware, software, data, people and procedures that work together to produce quality information.
There are 5 phases in system development life cycle:
- Planning
- Analysis
- Implementation
- Maintenance
General guidelines for system development:
- Group activities or task into phases.
- Involve users.
- Define standards.
Project management- process of planning, scheduling and controlling the activities during system development.
Analysis of project management:
- Project scope.
- Required activities.
- Time estimates for each activities.
- Cost estimates for each activities.
- Order of activities.
- Activities that can take place at the same time.
Feasibility- measure of how suitable the development of system will be to the organisation.
- Operational feasibility
- Schedule feasibility
- Technical feasibility
- Economic feasibility
Documentation- the collection and summarisation of data and information.
How data and information gathered?
- Review documentation.
- Observe.
- Survey.
- Interview.
- JAD (Joint Application Design) session.
- Research.
(1)The planning phase for a project begins when the steering committee receives a project request.
Four major activities are performed:
- Review and approve project requests.
- Prioritize the project requests.
- Allocate resources.
- Form a project development team.
(2)The analysis phase consists of two major activities:
- Conduct a preliminary investigation
- Perform detailed analysis
Process modeling (structured analysis and design) is an analysis and design technique that describes processes that transform inputs into outputs.
- Entity-relationship diagrams
- Data flow diagrams
- Project dictionary
An entity-relationship diagram (ERD) is a tool that graphically shows the connections among entities in a system
Entities are objects in the system that have data.
A data flow diagram (DFD) is a tool that graphically shows the flow of data in a system.
- Data flows
- Processes
- Data stores
- Sources
The project dictionary contains all the documentation and deliverables of a project
Structured English is a style of writing that describes the steps in a process
(3) The design phase consists of two major activities
- Acquire hardware and software
- Develop all of the details of the new or modified information system
The next step is to develop detailed design specifications
Sometimes called a physical design
- Database design
- Input and output design
- Program design
A prototype (proof of concept) is a working model of the proposed system
- Prototypes have inadequate or missing documentation
- Users tend to embrace the prototype as a final system
- Should not eliminate or replace activities
Computer-aided Software Engineering (CASE)- tools that are designed to support one or more activities of system development.
- Project repository.
- Graphics.
- Prototyping.
- Quality assurance.
- Code generator.
- Housekeeping.
(4) The purpose of the implementation phase is to construct the new or modified system and then deliver it.
- Develop programs
- Install and test the new system
- Train users
- Convert to the new system
Program Development Cycle
- Analyze requirements
- Design the solution
- Validate the design
- Implemetn the design
- Test the solution
- Document the solution
(5) Maintenance
- Perform maintenance activities- to maintain the lifetime of the system.
- Monitor system performance- to see if any improvement is needed.
- Assess system security- manage the security and keep it updated.
Computer security plan should have:
- Identify all information assets of an organisation.
- Identify all security risks that may cause an information asset loss.
- For each risk, identify the safeguards that exist to detect, prevent and recover from a loss.
Tuesday, 18 October 2016
CHAPTER 11
MANAGE COMPUTING SECURELY, SAFELY AND ETHICALLY
Computer Security Risk
A computer security risk is any event or action that could cause a loss of or damage to computer hardware, software, data, information, or processing capability
A cyber crime is an online or Internet-based illegal act.
Example of cyber crime:

Computer Security Risk
A computer security risk is any event or action that could cause a loss of or damage to computer hardware, software, data, information, or processing capability
A cyber crime is an online or Internet-based illegal act.
Example of cyber crime:
- HAckers
- Crackers
- Script kiddies
- Corporate spies
- Unethical employees
- Cyberterrorist
- Cyberextortionists
Internet and Network Attacks
- Computer virus
- Worm
- Trojan horse
- Rootkit
Firewall is hardware and/or software that protects a network’s resources from intrusion
Hardware theft is the act of stealing computer equipment
Hardware vandalism is the act of defacing or destroying computer equipment
Software Theft occurs when:
- Steals software
- Intentionally erases programme
- Illegally copies a programme
- illegally register and/or activate a programme
Information theft occurs when someone steals personal or confidential information
Encryption is a process of converting readable data into unreadable characters to prevent unauthorized access.
Security techniques
- Digital certificates
- Secure HTTP
- Transport Layer Secuirty(TLS)
- VPN
Backup is a duplicate of a file, program, or disk that can be used if the original is lost, damaged, or destroyed and to back up a file means to make a copy of it.
Offsite backups are stored in a location separate from the computer site such as in cloud storage.
Computer ethics are the moral guidelines that govern the use of computers and information systems.
Green computing is the environmentally responsible and eco-friendly use of computers and their resources. In broader terms, it is also defined as the study of designing, manufacturing/engineering, using and disposing of computing devices in a way that reduces their environmental impact.
A cookie is a
small text file that a Web server stores on your computer.
Purposes of using Cookies
- Allow for personalization
- Store user's password
- Assist with online shopping
- Track hows often users visit a site
- Target advertisments
CHAPTER 10
MANAGING DATABASES
Database
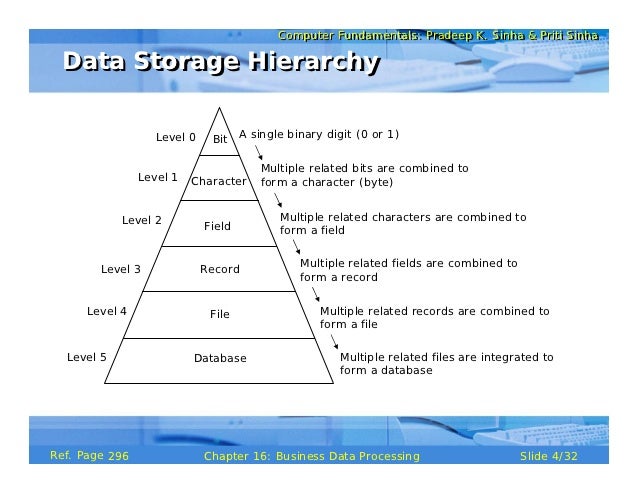
Hierarchy of Data
Database Design Guideline
Database design is the process of producing a detailed data model of database. This data model contains all the needed logical and physical design choices and physical storage parameters needed to generate a design in a data definition language, which can then be used to create a database. A fully attributed data model contains detailed attributes for each entity.
File maintanance
Data Management System (DBMS)
Database
- Collection of data organized in a manner that allows access, retrieval, and use of that data.
Data
- Collection of unprocessed item.
Examples
- Text
- Numbers
- Images
- Audio
- Video
Information
- Processed data
- Documents
- Audio
- Video
- Images
Valuable Information should have the following;
- Accurate
- Verifiable
- Timely
- Organized
- Accessible
- USeful
- Cost effective
Hierarchy of Data
- Bit
- Character
- Field
- Record
- File
- Database

Database Design Guideline
Database design is the process of producing a detailed data model of database. This data model contains all the needed logical and physical design choices and physical storage parameters needed to generate a design in a data definition language, which can then be used to create a database. A fully attributed data model contains detailed attributes for each entity.
- Determine the purpose of the database - This helps prepare for the remaining steps.
- Find and organize the information required - Gather all of the types of information to record in the database, such as product name and order number.
- Divide the information into tables - Divide information items into major entities or subjects, such as Products or Orders. Each subject then becomes a table.
- Turn information items into columns - Decide what information needs to be stored in each table. Each item becomes a field, and is displayed as a column in the table. For example, an Employees table might include fields such as Last Name and Hire Date.
- Specify primary keys - Choose each table’s primary key. The primary key is a column, or a set of columns, that is used to uniquely identify each row. An example might be Product ID or Order ID.
- Set up the table relationships - Look at each table and decide how the data in one table is related to the data in other tables. Add fields to tables or create new tables to clarify the relationships, as necessary.
- Refine the design - Analyze the design for errors. Create tables and add a few records of sample data. Check if results come from the tables as expected. Make adjustments to the design, as needed.
- Apply the normalization rules - Apply the data normalization rules to see if tables are structured correctly. Make adjustments to the tables.
File maintanance
- Adding records
- Modifying records
- Deleting records
Validation
- Alphabetic/Numeric check
- Range check
- Consistency check
- Completeness check
- Check digit
- Other checks
- Query language
- Query by example
- Form
- Report generator
Databases on the Web allows you to:
- Shop for products
- Buy or sell stocks
- Search for a job
- Make airline reservation
- Register for college
- Check semesters grades
CHAPTER 9
NETWORKS AND COMMUNICATIONS
Communication
Computer communications describes a process in which two or more computers or devices transfer data, instructions, and information.
Uses Computer communication



Types of wired home networks
Types of Physical Transmission Media

Communication
Computer communications describes a process in which two or more computers or devices transfer data, instructions, and information.
Uses Computer communication
- Text messaging (sms)
- picture messaging
- video messaging
- Gps
- groupware
- voicemail
Networks
A network is a collection of computers and devices connected together via communications devices and transmission media
Advantages of a Network
- Facilitating communication
- sharing hardware
- sharing data and information
- sharing software
- transferring funds
Types of networks
- Local Area Network (LAN)
- Wireless LAN (WLAN)
- Metropolitan Area Network (MAN)
- Wide Area Network(WAN)
- P2P
Network Topology
Network topology is the arrangement of the various elements (links, nodes, etc.) of a computer network. Essentially, it is the topological structure of a networkand may be depicted physically or logically.
Networks
- Ethernet
- Token ring
- TCP/IP
- Wifi
- Bluetooth
- UWB
- IrDA
- RFID
- WiMAX
- WAP
Types of wired home networks
- Ethernet
- Powereline Cable
- Phoneline
Types of Physical Transmission Media
- Coaxial cable
- Twisted pair
- Fibre optics

Types of Wireless Transmission Media
- Infrared
- Broadcast Radio
- Cellular Radio
- Microwave Radio
- Communication Satelite
Subscribe to:
Comments (Atom)